Heya, I found how you can digitally sign and encrypt emails! (It even gives them a cool icon for others to see!), and I haven't seen anything about it before so I thought I'd share how I did it!
Do you also want to send encrypted emails and sign them? Just follow these few steps!
But beforehand, let's define some terms :
-
Signed email : Email with a valid numerical signature. Anyone can read it and know it has not been modified since it was sent.
-
Encrypted email : Email encrypted with the recipient's public key. They can decrypt it with their private key
-
S/MIME certificate : A
.p12file containing your private key (So keep it for yourself and don't send it to anyone!!) and your public key.
Okay, now it's time to...
Start the setup (Obtain an S/MIME certificate)
- You'll need to ask to an authority for a certificate. Personally I use Actalis because they give free certificates for multiple email addresses, valid for a year (you need to redo the setup every year). If you don't want to use Actalis, more info is avilable here.
- Don't forget to put the website in english if you don't understand italian.
- Go on the page to request an S/MIME certificate, create an account and follow the setup. The verification email can take a little while (~2min)
- When the setup ends, you'll have a valid certificate in your dashboard (It can take a few minutes to appear if you just verified it) that you can download, and a password that Actalis emailed you to enable your certificate.
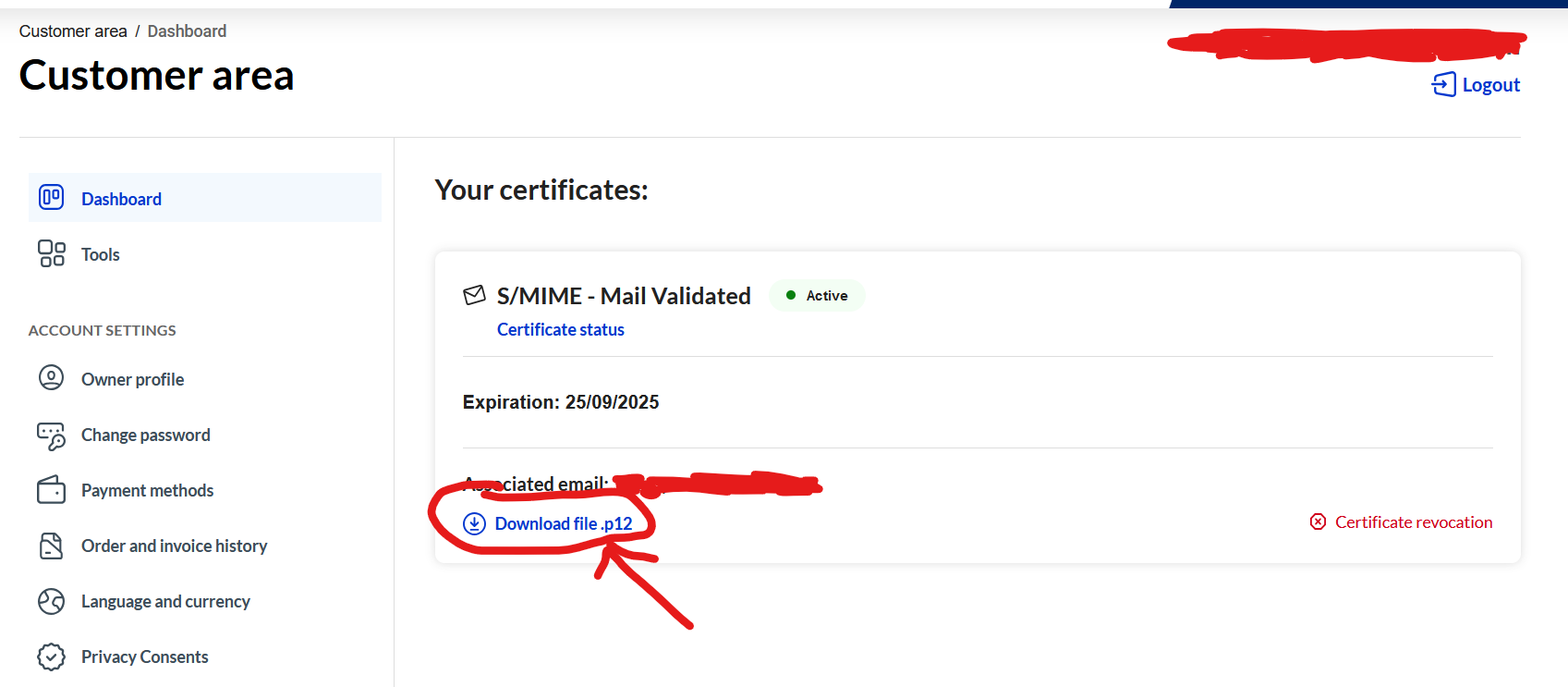
Install the certificate
- Download the .p12 file, then open it, type your password, and leave the default options to install the certificate on your device (Android or PC, on Android pick "For VPN and apps"). Don't delete your old one, so you can still decrypt old messages sent on the expired certificate
- Use an S/MIME compatible email client. On PC, there is Thunderbird, on Android, FairEmail.
- In your email client settings, importer the S/MIME certificate pofor signing AND encrypting your messages. It changes depending on your client, so here it is for Thunderbird :
- In the top-right menu, go to
Account settings,End-to-end encryption, underS/MIMEclick onManage S/MIME certificates,Importand pick your.p12file. Then, pickSelect a certificate, and pick yours from the tab "Your certificates".
- In the top-right menu, go to
An image is worth a thousand words (Sorry for the french)
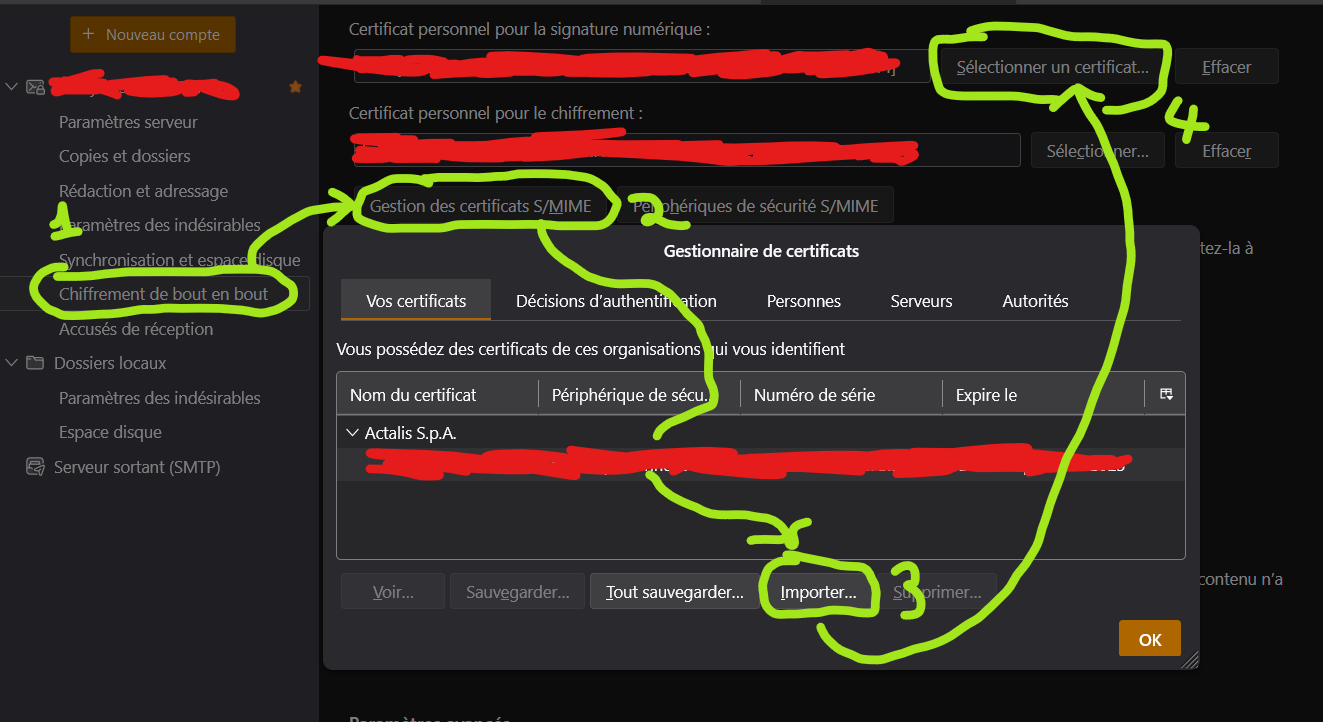
Don't forget to check the box to sign and/or encrypt every message just below, if you want!
Communicate with someone
Once this is done, here is how you can communicate...
- ...While signing your messages :
It's easy, just click on "Sign" before sending. Usually, email clients show a small medal next to your name to show the email is signed.
- ...While encrypting your messages :
For that, you'll need your recipient's public key. They needs to send you a signed message (not encrypted, since you don't have each other's key at this point) where you can get their public key from their signature, and add it to your email client, which will allow you to encrypt messages you send to them. Then, send them a signed email (you can encrypt it) so they can get your public key and add it to their client, and then you'll be able to exchange encrypted emails!
I'm not an expert and probably made a few mistakes, if you spot any please tell me in the comments and I'll try to fix the guide!
Personally I'd love to see more wider usage of S/MIME and/or PGP. What I take issue with actalis, is that they don't just sign your private key but you actually get the private key from them. It then depends on how much you trust the issuer. To me a key that wasn't always in your possession is basically compromised from the start.
(Although, I am also using protonmail's pgp, which arguably violates this rule as well, their transparency is more trustworthy to me. )
I'd rather see less. https://www.latacora.com/blog/2019/07/16/the-pgp-problem/ is a good summary about the issue and they have a shorter follow-up post about why encrypting mail in general is bad at https://www.latacora.com/blog/2020/02/19/stop-using-encrypted/
By definition, that key can no longer be considered "private".
It is very important to emphasize that the key in this model is not "private" anymore. Thus, all the communication using this key is not secure anymore.
Private key is the one generated by hardware owned by the user and immediately secured with strong password. Ideally, private key does not leave the hardware that generated it. Thus, every device shall have its own private key.
In less restricted model, private key gets copied by the user to other hardware using media like USB stick or P2P communication model that does not use cloud services.
Good counter discussion about PGP security
https://www.reddit.com/r/cryptography/comments/10cfslk/exactly_how_strong_is_pgp/
I would argue that latacora could be an attempt to push users into the systems that provide 3rd party service, which by definition of 3rd party service is not secure: WhasApp, Signal.
Only true P2P can be safe. PGP provides ability to send encrypted message using any means necessary: FTP, HTTP, anonymous services, USB sticks, anything.
Those are some very good points. Some even eye opening to me. It seems that my viewpoint probably was a bit skewed as the email encryption I mostly deal with is between businesses as part of my day job. I guess, in that context things like the meta data issue are known but accepted as the relationships between parties in most cases are public knowledge and companies may have to keep records for LE/regulatory bodies anyway. I can also see how quite a bit of it could be considered performative.
I hadn't considered much that advocating for encrypted email outside of that context could keep people from using the right tool for their needs and possibly hinder acceptance of better choices.
The PGP article also made me roll my eyes a bit, as one of our vendors still doesn't support ECC keys today. The last reason communicated being that the relevant RFC was only a draft.
The point about email having leaking matadata is 100% spot on.
The argument why Signal is better is very short and not substantiated IMO.